
Lockbit 3.0: A threat to corporate IT security
Ransomware with a global reach
Since its appearance in 2019, Lockbit 3.0 has been one of the most formidable ransomware programs in the digital world. With over 1700 attacks listed worldwide since 2020, including renowned companies such as Thales, Continental and TSMC, its presence poses a serious threat to organizations IT security.
Decline of a giant
February 20, 2024 marked a turning point in the fight against this threat, with the dismantling of Lockbit during a vast international police operation named 'cronos'. Coordinated by Europol and the National Crime Agency, this investigation launched in 2022 resulted in the seizure of almost 200 crypto-currency wallets, the dismantling of 34 servers and the recovery of over 1,000 decryption keys worldwide.
Following this intervention, the LockBit 3.0 showcase site was no longer accessible, nor was the portal used for negotiations. Instead, an image was displayed with the message: "This site is now under law enforcement control".
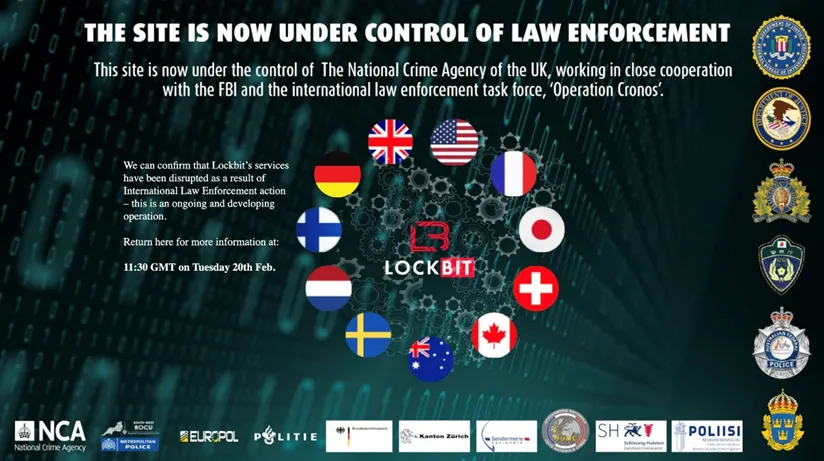
An unexpected comeback
However, despite these efforts, Lockbit is still active. On February 25, 2024, the group relaunched its activities with a new showcase site based on the same structure as the old one, with already, new victims. In addition, a statement against the FBI and the 'cronos' operation was released.
Lockbit examined the vectors that facilitated the law enforcement operation. The head of the group acknowledged his errors, admitting "negligence" and "lack of responsibility" in delaying the update of Lockbit PHP servers. This oversight gave the authorities the opportunity to exploit a security flaw in the PHP programming language.





